Understanding Your Computer Operating System
A working gadget (OS for brevity) is accountable for the coordination, management of activities, and useful resource sharing in a computer....
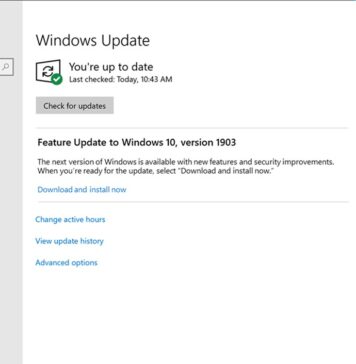
Installing the Chrome Operating System
General geekiness observed me trying to get the Chrome OS going for walks this weekend. It took quite a chunk of...
Smart Card Operating System Development
Smart card chip operating machine (COS) has traditionally been designed with no precise application in thoughts. However, there are a few...
Operating Systems
Introduction
Linux OS was first created utilizing a student from the University of Helsinki in Finland. The creator's name changed into Linus...
How to Install Operating System Without CD or Through the Network
Introduction
In this article, you will study how to install the Operating System without a CD or through the Network. Before reading...
Windows Phone Operating System
Windows Phone is the most modern running device in the marketplace. Windows Phone has validated that specifications no longer remember if...
How an Operating System’s File System Works
File systems are an essential part of any working structures with the capability for a long time garage. There are wonderful...
A New View on Operating Systems and the Wold Wide Web
1. Introduction
The contemporary answers for PaaS, IaaS or SaaS, revolve around the idea of cloud computing and every so often virtualization....
Web Site Promotion – What Will Be the Effect of the Google Chrome Operating...
Web Site Promotion - Google Chrome Operating System
What may be the effect of Google's new Chrome Operating machine on internet website...
How to Build a Successful Online Operating System
We will talk about how to build a successful online operating system. You will learn about the history of OSS and...